All three stories are about control of the edge: bases harden skies with layered C-UAS; the living-room screen morphs into an AI-commerce endpoint; and a core internet plumbing vendor faces a nation-state breach. Investor playbook: buy the mid-layer bottlenecks (sensors/fusion for C-UAS, on-device AI + measurement for TV-commerce, zero-trust/IR for cyber), and trade the policy/notification calendar (Golden Dome pilots, DirecTV/Glance launch windows, CISA directives and vendor 8-Ks).
Good: AeroVironment brings counter-drone shield to Grand Forks AFB
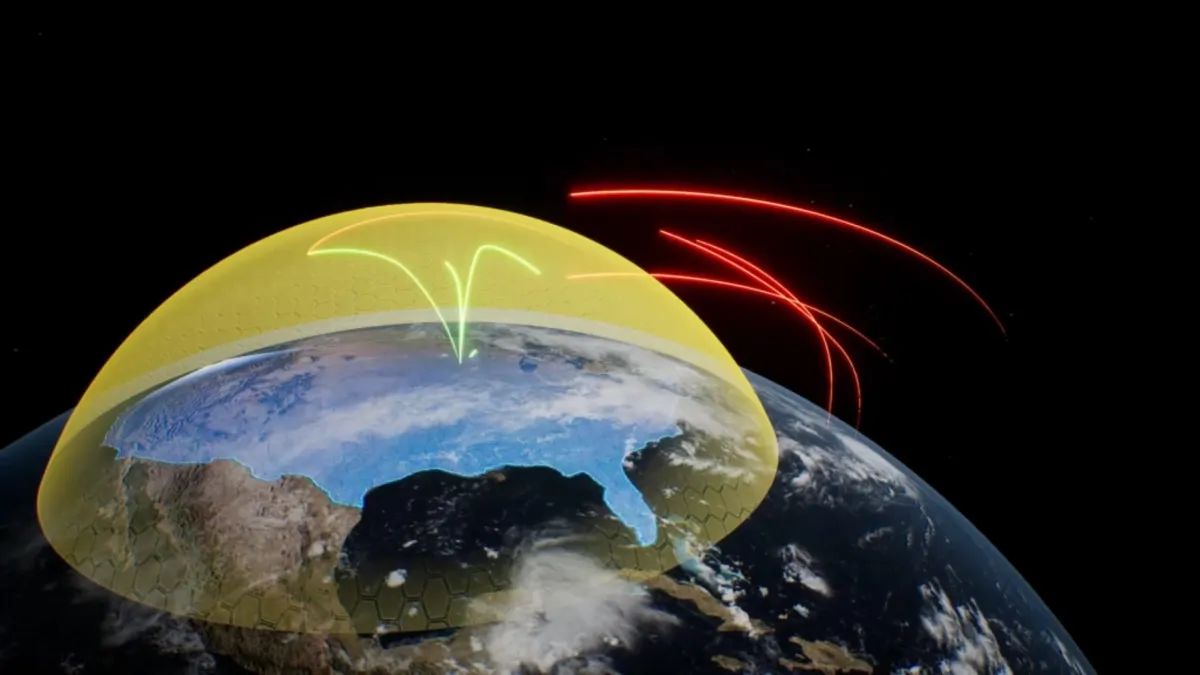
What it is:
AeroVironment is standing up a counter-UAS “inner layer” at Grand Forks Air Force Base (ND) with its Titan / Titan-SV RF sensors tied together by the AV Halo Command platform to give one fused air picture beyond visual line of sight. The project plugs into North Dakota’s Grand Sky UAS park and, per the company, lays groundwork for contributions to the wider “Golden Dome for America” air/missile defense concept. Defense News
What it will do:
- From demos to doctrine: A base-scale install lets the Air Force validate 24/7 detect-ID-track against small UAS, drones with weird signatures, and swarm tactics — the stuff showing up over Ukraine and the Middle East.
- Open architecture momentum: AV is positioning this as a node inside a larger, layered defense that could add EW, directed energy, and kinetic effectors over time. Interop becomes a procurement lever.
- Homeland defense ripple: If it works at Grand Forks, expect copy-paste to other critical sites (bases, ports, power plants).
How you can benefit:
- Own sensors & fusion, not just shooters: Look at suppliers in RF detection, EO/IR, radars, sensor fusion software, and command-and-control that slot into layered C-UAS; they win whether the effector is a jammer, DE laser, or interceptor. Avinc
- Regional build-out plays: North Dakota’s UAS corridor and Grand Sky ecosystem are pulling companies and grants; track local integration/MRO and range services providers.
- Follow the program names: Any official Golden Dome pilot awards would be catalysts for RF/cyber-EW vendors tied to AV’s stack.
Bad: DirecTV is turning ad breaks into shoppable, AI-avatar cameos
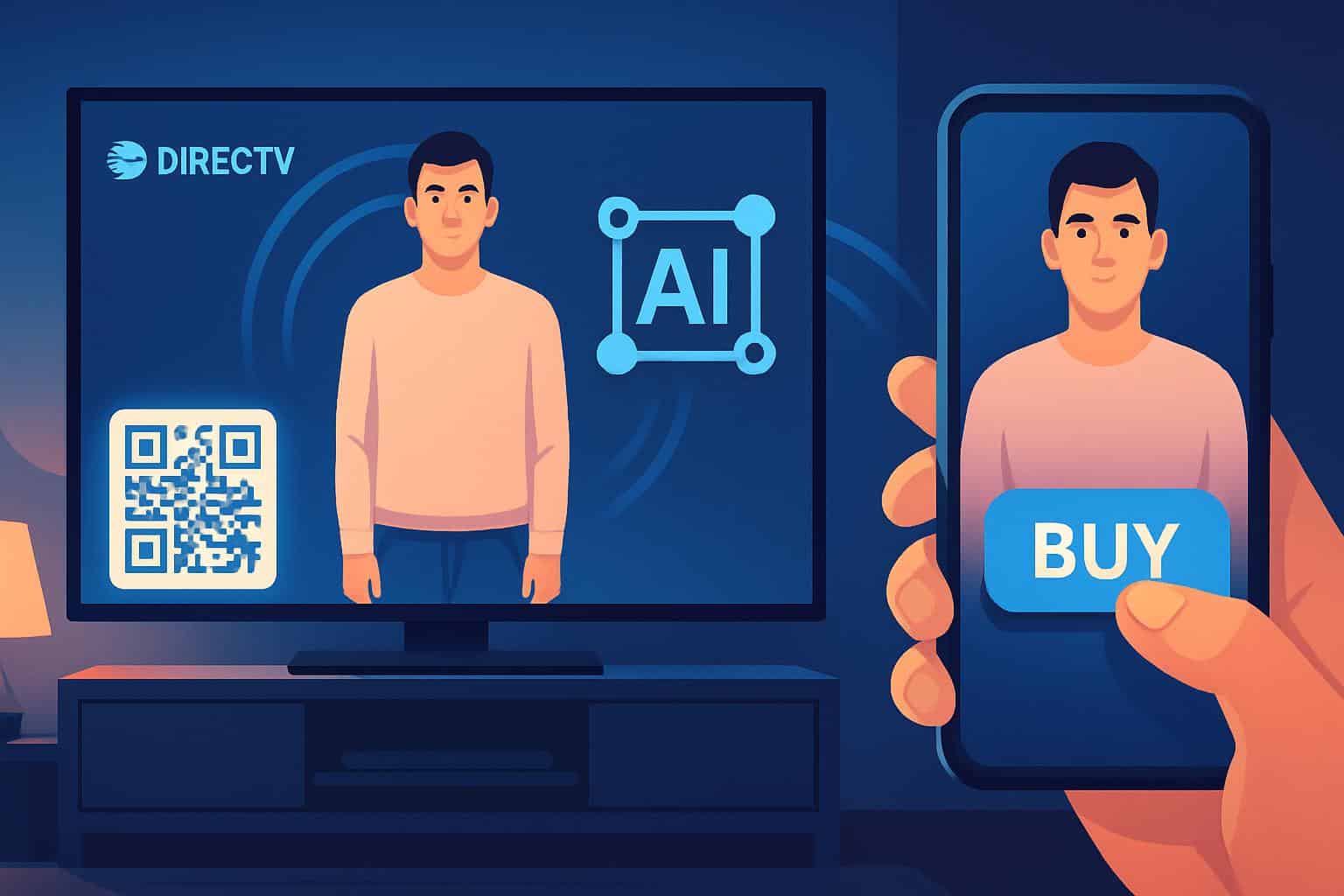
What it is:
DirecTV is partnering with Glance to roll out AI-generated, personalized screensavers/avatars on Gemini devices starting in 2026. Think: your TV’s idle screen becomes an interactive scene that can include AI versions of you/family/pets, voice-driven restyling, and QR-to-phone checkout for “similar” products in the scene. It’s the push to turn TVs from lean-back to lean-in commerce.
What it will do:
- New retail funnel: The living-room glass becomes a first-party shopping surface with measurable attribution — a big deal for TV ad economics. The Verge
- Privacy & consent pressure: If faces and rooms inform recommendations, age-gating, consent, and profiling controls will be under a microscope. The Verge
- Creative supply chain changes: Brands/agencies will need avatar-ready assets and pipelines for dynamic product substitution (AI finding “look-alike” items in real time).
How you can benefit:
- Pick-and-shovel adtech: Names in identity/consent management, on-device AI, visual search, and commerce checkout should see pull-through as TV becomes shoppable.
- Measurement & ACR: Automatic content recognition/measurement vendors that tie TV exposure to conversion will be critical — watch for DirecTV/Glance analytics partners.
- Privacy/regtech hedge: A parallel bet in privacy compliance/age-verification offsets regulatory risk as avatar ads scale.
Ugly: “Potentially catastrophic” breach at cybersecurity firm tied to China

What it is:
Bloomberg reported — and Reuters echoed — that U.S. cybersecurity vendor F5 suffered a long-running breach attributed to China-linked actors, with the intrusion allegedly persisting for ~12 months. Axios previously noted source code theft and emergency CISA attention given how widely F5’s Big-IP products sit in federal/enterprise networks. F5 said operations continue, but U.S. agencies flagged imminent risk for gov systems using its gear.
What it will do:
- Downstream blast radius: If adversaries touched source code/configs, expect supply-chain and zero-day concerns across customers until patches and hunts are complete. Axios
- Policy & procurement blowback: Federal buyers may accelerate software bill of materials (SBOM) demands, secure-by-design attestations, and continuous monitoring for vendors in the traffic-management stack.
- China attribution escalates risk: As more incidents are pinned on PRC-linked operators, expect sanctions/export-control chatter and higher cyber insurance costs sector-wide.
How you can benefit:
- Own the “assume breach” toolchain: Identity/zero-trust, EDR/XDR, log analytics, threat intel, and SBOM scanners get budget reallocated in crises like this.
- Incident-response & audit winners: IR shops and managed detection/response providers see near-term service spikes; some convert to longer-term MSSP contracts.
- Credit/partner hygiene screen: For exposed vendors/customers, watch 8-K cyber filings, CISA directives, and patch SLAs — tradable catalysts for both upside (fast responders) and downside (laggards).